

Secuware Security Framework (SSF)
Building on the solid foundation of C2K, SSF extends the security of Windows networks by creating closed circuits for information in which only authorized individuals using authorized devices and authorized applications can access authorized data, preventing information leakage and delivering a more stable computing environment.
Secuware SSF Data Sheet ![]()
SSF returns control of the network to the enterprise by delivering:
- A secure operating system, not just access control and encryption.
- Flexible architecture that enables protection to adapt as behaviors, threats, and systems evolve.
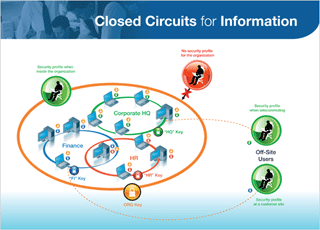
- Closed circuits of information - security zones within and beyond the borders of the enterprise
- Assured compliance through the prevention of information leakage and blocking of malware.
- Scalability and simplified policy deployment through tight integration with Windows and major directory services.
- Enhanced internal security by separating IT and information security controls.
Multi-Dimensional Security
SSF delivers true multi-dimensional security that’s always-on:
Security Right from the Start
- Systems are protected from boot process onwards.
- Protection cannot be bypassed by low-level access tools.
 |
- Users get the access they need to do their jobs.
- Information is protected within defined groups.
Devices are Locked Against Unauthorized Access
- All storage device types - hard drives, USB drives,
CD and DVD drives.
- Authorized users retain transparent access.
Logical Encoding of Data in Network Folders
- Protected data remains protected, wherever it is stored.
- Encoded data not accessible to administrators – or malware.
Increased Stability of Software and Hardware
- Software authorization.
- Authorization of devices.
SSF’s modular framework delivers 360 degrees of security in a single suite that adapts to changing threats, behaviors, and systems over time:
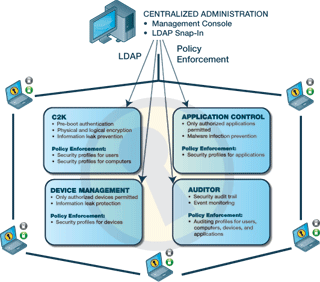 |
C2K is at the heart of SSF. It sets up access control before booting the operating system and encrypts all the information stored on the computer as well as any information that could be copied through the use of another device. C2K ensures that the computer and all the data and applications stored on that computer may only be used by authorized individuals.
The Devices module controls which devices are permitted to connect to the network and the type of connections those devices may make. Its role is to prevent unauthorized hardware devices such as CD or DVD burners, USB drives, and other removable media from connecting to enterprise systems and introducing malware infections or removing confidential information.
The Applications module enables IT departments to take a snapshot of all applications and other components installed on any given computer for the purposes of validation. Once the snapshot has been acquired, only validated applications can be executed on that computer. Use of the Applications module ensures the stability of the computer, protects it from integrity threats such as viruses and Trojans, reduces demands on the helpdesk, and assists in controlling and forecasting maintenance costs.
The Auditor module creates a log of all security events recorded by SSF in order to provide a comprehensive security audit trail for compliance and forensics purposes. The data supplied by the Auditor module can be used to refine security policies to more accurately reflect the organization’s needs and any given point in time.


