

Secuware C2K
 Network endpoints – whether desktops, laptops, or PDAs – are loaded with critical data that can – as we read in the news almost every day – be lost, stolen, or hijacked in any number of ways. C2K protects that critical data more powerfully, and more transparently to users, than any solution currently on the market. Originally developed for the Spanish Defense Ministry, C2K really does offer military-grade security for your critical corporate data.
Network endpoints – whether desktops, laptops, or PDAs – are loaded with critical data that can – as we read in the news almost every day – be lost, stolen, or hijacked in any number of ways. C2K protects that critical data more powerfully, and more transparently to users, than any solution currently on the market. Originally developed for the Spanish Defense Ministry, C2K really does offer military-grade security for your critical corporate data.
- C2K’s Pre-Boot Authentication (PBA) accepts digital certificates, smart cards, or USB tokens as valid user identification. If no acceptable identification is supplied, the boot process is terminated.
- Complete physical and/or logical encryption of hard disks and removable media prevents the computer from being booted by alternate means, even if the would-be thief has physical access to the media using a different computer.
Closed Circuits for Information (CCI)
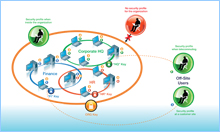 |
Complete physical hard disk encryption
The only way to ensure that all the information is protected is the complete physical encryption of the hard disk. Encrypting all the hard disk's physical sectors protects even temporary files and traces remaining on the disk that could be otherwise exploited by unauthorized users.
Information encryption over the network
Today’s file systems offer a high level of access control, but any user with administrator privileges can access any other user's information. No matter how thorough your security policy, any document stored unencrypted on the network is readable by anyone with admin-level permissions. C2K encompasses any storage resources used by employees and contractors, including shared folders on the network. So when users store information on the network, that information is encrypted and protection is assured.
Public Key Infrastructure (PKI) integration
C2K is PKI ready and as such can perform secure logon using digital certificates provided by any vendor based on the X.509 v3 and LDAP x.500 standards. Combining Pre Boot Authentication and the use of digital certificates on physical access tokens provides maximum access control by enforcing network-wide user identification and validation.


